Overview
This article provides an overview of the Incydr cloud and insider risk agent architecture. It includes diagrams that identify and illustrate how the major components of the Incydr cloud are organized into a comprehensive and secure solution.
File event data collection
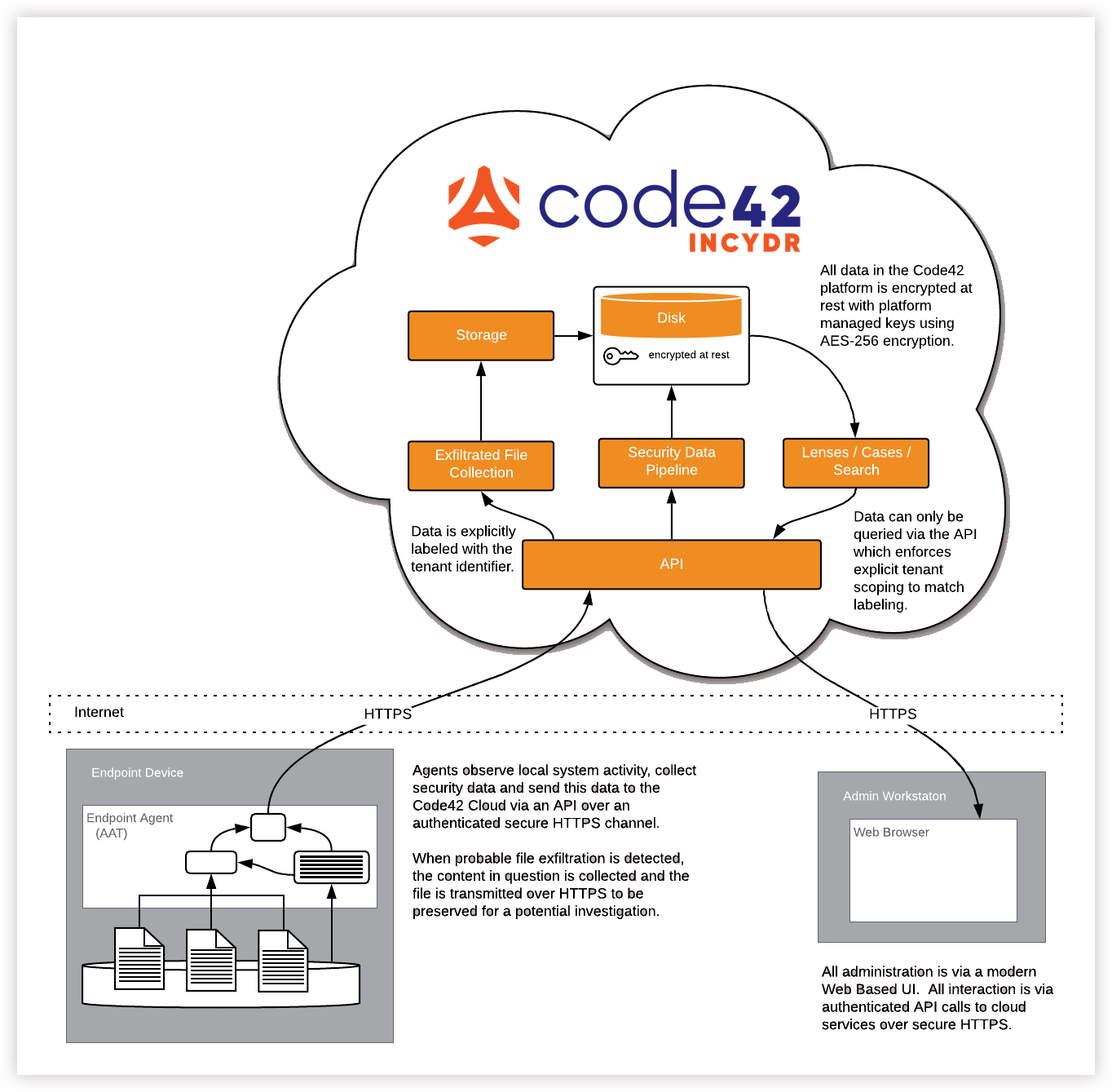
The insider risk agent on the endpoint (also known as the "agent") observes user and file system activity in order to identify file-related events. This data is transmitted to the Incydr cloud over secure and authenticated HTTPS with Transport Layer Security (TLS) utilizing AES-256 cipher suites. All submitted data is explicitly labeled with the tenant identifier to ensure integrity and privacy of each customer's data. The events are processed within a pipeline that enriches the data with context information for use in alerts, detection lists, and searches. This indexed data is encrypted at rest using AES-256. When the agent detects probable file exfiltration, a copy of the file in question may be captured and sent to the cloud via HTTPS and preserved, encrypted at rest, to support a potential investigation. This data is only accessible via authenticated HTTPS APIs, and all tenant labels are validated on data access.
Endpoints do not need to stay inside a corporate network to send data to the Incydr cloud; no VPN, port forwarding, or DMZ is needed. The Incydr cloud architecture is designed for ubiquitous secure access.
Content inspection
Content inspection is an optional component of Exfiltrated File Collection and adheres to the same strict security architecture as outlined above. For more details, see Content inspection security architecture.
Extended cloud architecture
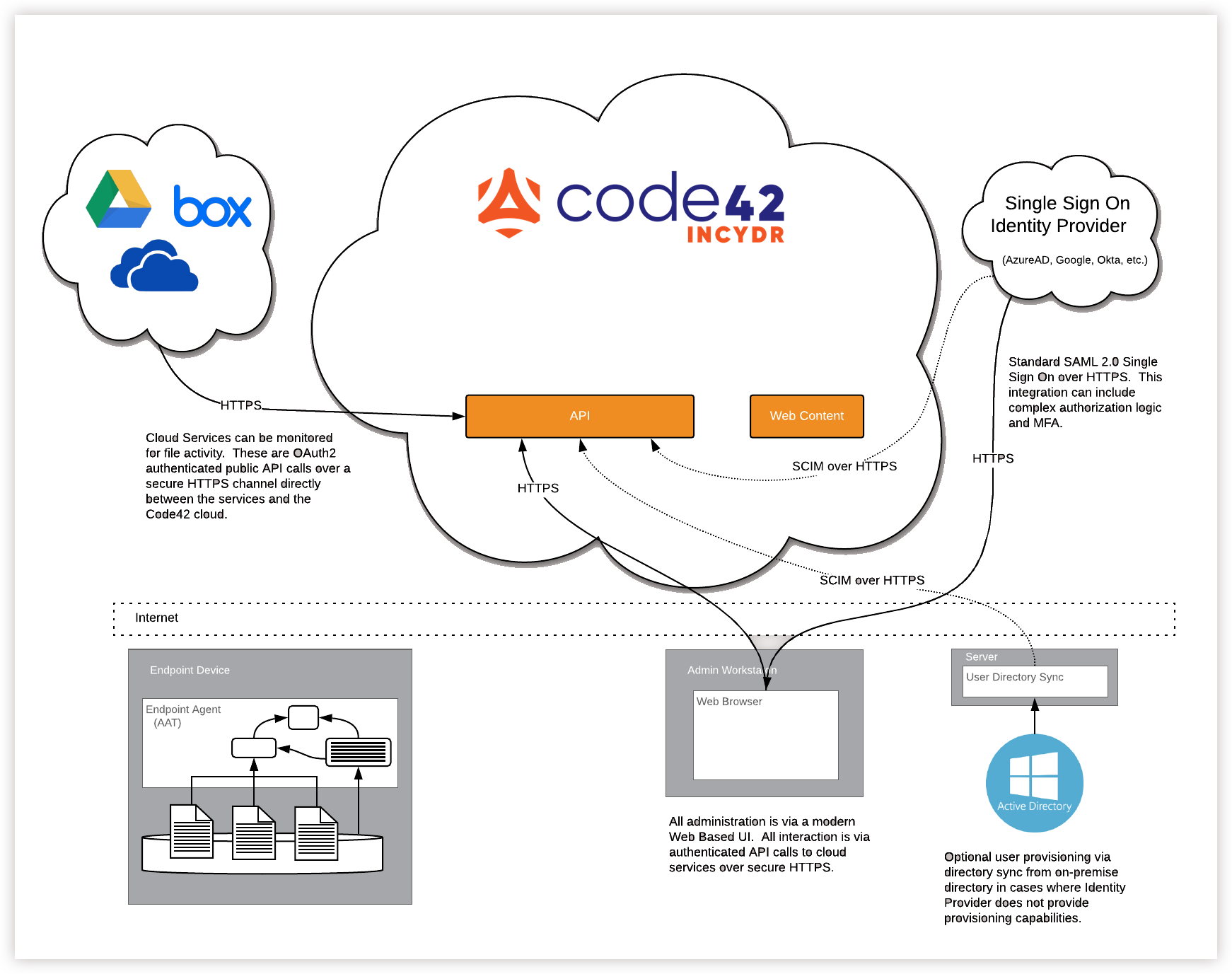
The Incydr cloud is extensible and integrates with other cloud services. The Incydr cloud:
- Monitors file activity on other cloud services similar to how it monitors file activity on endpoints.
- Supports SAML 2.0 protocol for single sign-on.
- Supports SCIM for synchronizing directory updates and automated provisioning.
- Provides apps that integrate with SOAR and SIEM solutions.
- Provides public APIs for you to build your own integrations.
Agent architecture
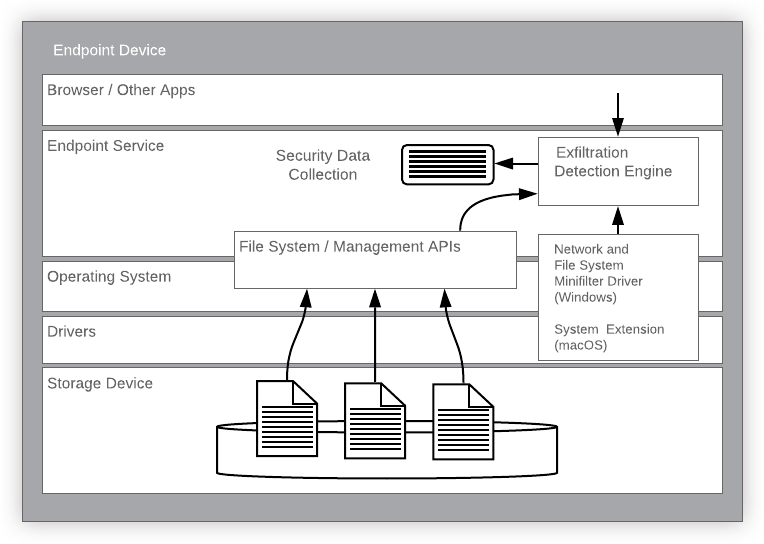
The insider risk agent on the endpoint (also known as the "agent") executes as a service. The agent interacts with platform or operating system APIs to observe system activity related to file movement, and collects and submits the resulting data to the Incydr cloud. Data is submitted to the cloud over an authenticated HTTPS channel.
Related topics
Comments
Please sign in to leave a comment.